Дисертації з теми "Quantum random oracle model"
Оформте джерело за APA, MLA, Chicago, Harvard та іншими стилями
Ознайомтеся з топ-26 дисертацій для дослідження на тему "Quantum random oracle model".
Біля кожної праці в переліку літератури доступна кнопка «Додати до бібліографії». Скористайтеся нею – і ми автоматично оформимо бібліографічне посилання на обрану працю в потрібному вам стилі цитування: APA, MLA, «Гарвард», «Чикаго», «Ванкувер» тощо.
Також ви можете завантажити повний текст наукової публікації у форматі «.pdf» та прочитати онлайн анотацію до роботи, якщо відповідні параметри наявні в метаданих.
Переглядайте дисертації для різних дисциплін та оформлюйте правильно вашу бібліографію.
Fallahpour, Pouria. "Lattice-based cryptography in a quantum setting : security proofs and attacks." Electronic Thesis or Diss., Lyon, École normale supérieure, 2024. http://www.theses.fr/2024ENSL0023.
Повний текст джерелаThe rise of quantum machines poses both challenges and opportunities for cryptography. In particular, security proofs may require revisions due to adversaries' quantum capabilities. This thesis presents two contributions in this respect: a positive result and a negative one. The Fiat-Shamir transform with aborts is one of the major paradigms for designing post-quantum secure signature schemes. Part of this thesis consists of a detailed security analysis of this transform in the quantum random oracle model. It is worth noting that all previous works have neglected subtle details, jeopardizing the correctness of their proofs. Consequently, our security proof stands as the first of its kind that is correct. Moreover, we analyze the runtime and correctness of the signatures obtained from this transform. The learning with errors (LWE) problem has been extensively utilized to construct cryptographic schemes that are secure against quantum adversaries. A knowledge assumption of the LWE problem states that obliviously sampling an LWE instance, namely without knowing its underlying secret, is hard for all polynomial-time algorithms. One can use this assumption to prove the security of some succinct non-interactive arguments of knowledge (SNARKs). While it seems a hard task for classical algorithms, we demonstrate a quantum polynomial-time oblivious LWE sampler. Consequently, our sampler breaks the security analysis of the mentioned SNARKs in the quantum setting
Aronsen, Kristoffer. "Quantum Criticality in the Transverse Field Random Ising Model." Thesis, KTH, Fysik, 2019. http://urn.kb.se/resolve?urn=urn:nbn:se:kth:diva-257771.
Повний текст джерелаCao, Zhenwei. "Quantum evolution: The case of weak localization for a 3D alloy-type Anderson model and application to Hamiltonian based quantum computation." Diss., Virginia Tech, 2012. http://hdl.handle.net/10919/19205.
Повний текст джерелаPh. D.
Björnberg, Jakob Erik. "Graphical representations of Ising and Potts models : Stochastic geometry of the quantum Ising model and the space-time Potts model." Doctoral thesis, KTH, Matematik (Inst.), 2009. http://urn.kb.se/resolve?urn=urn:nbn:se:kth:diva-11267.
Повний текст джерела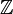 . In Chapter 3 we develop an alternative graphical representation of the quantum Ising model, called the random-parity representation. This representation is based on the random-current representation of the classical Ising model, and allows us to study in much greater detail the phase transition and critical behaviour. A major aim of this chapter is to prove sharpness of the phase transition in the quantum Ising model—a central issue in the theory— and to establish bounds on some critical exponents. We address these issues by using the random-parity representation to establish certain differential inequalities, integration of which gives the results. In Chapter 4 we explore some consequences and possible extensions of the results established in Chapters 2 and 3. For example, we determine the critical point for the quantum Ising model in
. In Chapter 3 we develop an alternative graphical representation of the quantum Ising model, called the random-parity representation. This representation is based on the random-current representation of the classical Ising model, and allows us to study in much greater detail the phase transition and critical behaviour. A major aim of this chapter is to prove sharpness of the phase transition in the quantum Ising model—a central issue in the theory— and to establish bounds on some critical exponents. We address these issues by using the random-parity representation to establish certain differential inequalities, integration of which gives the results. In Chapter 4 we explore some consequences and possible extensions of the results established in Chapters 2 and 3. For example, we determine the critical point for the quantum Ising model in 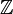 and in ‘star-like’ geometries.
and in ‘star-like’ geometries.HTML clipboard Statistisk fysik syftar till att förklara ett materials makroskopiska egenskaper i termer av dess mikroskopiska struktur. En särskilt intressant egenskap är är fenomenet fasövergång, det vill säga en plötslig förändring i de makroskopiska egenskaperna när externa förutsättningar varieras. Två modeller är särskilt intressanta för en matematiker, nämligen Ising-modellen av en magnet och perkolationsmodellen av ett poröst material. Dessa två modeller sammanförs av den så-kallade fk-modellen, en slumpgrafsmodell som först studerades av Fortuin och Kasteleyn på 1970-talet. fk-modellen har sedermera visat sig vara extremt användbar för att bevisa viktiga resultat om Ising-modellen och liknande modeller. I den här avhandlingen studeras den motsvarande grafiska strukturen hos två näraliggande modeller. Den första av dessa är den kvantteoretiska Isingmodellen med transverst fält, vilken är en utveckling av den klassiska Isingmodellen och först studerades av Lieb, Schultz och Mattis på 1960-talet. Den andra modellen är rumtid-perkolation, som är nära besläktad med kontaktmodellen av infektionsspridning. I Kapitel 2 definieras rumtid-fk-modellen, och flera probabilistiska verktyg utforskas för att studera dess grundläggande egenskaper. Vi möter rumtid-Potts-modellen, som uppenbarar sig som en naturlig generalisering av den kvantteoretiska Ising-modellen. De viktigaste egenskaperna hos fasövergången i dessa modeller behandlas i detta kapitel, exempelvis det faktum att det i fk-modellen finns högst en obegränsad komponent, samt den undre gräns för det kritiska värdet som detta innebär. I Kapitel 3 utvecklas en alternativ grafisk framställning av den kvantteoretiska Ising-modellen, den så-kallade slumpparitetsframställningen. Denna är baserad på slumpflödesframställningen av den klassiska Ising-modellen, och är ett verktyg som låter oss studera fasövergången och gränsbeteendet mycket närmare. Huvudsyftet med detta kapitel är att bevisa att fasövergången är skarp—en central egenskap—samt att fastslå olikheter för vissa kritiska exponenter. Metoden består i att använda slumpparitetsframställningen för att härleda vissa differentialolikheter, vilka sedan kan integreras för att lägga fast att gränsen är skarp. I Kapitel 4 utforskas några konsekvenser, samt möjliga vidareutvecklingar, av resultaten i de tidigare kapitlen. Exempelvis bestäms det kritiska värdet hos den kvantteoretiska Ising-modellen på
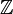 , samt i ‘stjärnliknankde’ geometrier.
, samt i ‘stjärnliknankde’ geometrier.QC 20100705
Sugishita, Sotaro. "Construction of a new model generating three-dimensional random volumes:Towards a formulation of membrane theory." 京都大学 (Kyoto University), 2016. http://hdl.handle.net/2433/215308.
Повний текст джерелаCharbonnier, Séverin. "Liouville theory and random maps." Thesis, Université Paris-Saclay (ComUE), 2018. http://www.theses.fr/2018SACLS265/document.
Повний текст джерелаThis thesis explore several aspects of random maps through the study of three models. First, we examine the properties of a measure defined on the set of planar Delaunay triangulations with n vertices, a model in which the edges of the maps are decorated with angles. We show that the measure is the Weil-Petersson volume form on the moduli space of planar Riemann surfaces having n marked points. Two other properties, first steps toward the continuous limit study of the model, are also shown. Second, we define correlation functions on isoperimetric planar Strebel graphs with n faces, which are trivalent maps whose edges are decorated by positive lengths, and whose faces have a fixed perimeter. Kontsevich's theorem allows us to compute the correlation functions in terms of the intersection numbers of Chern classes of moduli space of Riemann surfaces. The continuous limit of the one-point function is computed in different regimes for the perimeter of the marked face via the saddle-point approximation. We identify the regime in which the behaviour of the one-point function is not trivial. The correlation functions can be computed in a systematic way by the Topological Recursion. To do so, we compute the spectral curve of the model, and show that there exists a critical spectral curve. We deduce from the latter that the continuous limit of isoperimetric Strebel graphs is a (3,2) minimal model dressed by Liouville theory: it corresponds to pure gravity. Last, we address the problem of symmetries in the Ising model on random maps. Some correlation functions of this model count the bi-colored maps with marked faces having mixed boundary conditions. They are computed via a recursive formula and the spectral curve of the model. We prove here that the correlation functions of maps with one mixed boundary, computed from the recursive relation with generic spectral curve, are invariant under rotation and inversion of the mixed boundary. We describe the consequences of such symmetries, suggesting a possible reformulation of the model in terms of spin chains
Palaniswamy, Basker. "Improving authentication and key management for intra and inter vehicular communication." Thesis, Queensland University of Technology, 2022. https://eprints.qut.edu.au/236249/1/Basker%2BPalaniswamy%2BThesis.pdf.
Повний текст джерелаKuppusamy, Lakshmi Devi. "Modelling client puzzles and denial-of-service resistant protocols." Thesis, Queensland University of Technology, 2012. https://eprints.qut.edu.au/61032/1/Lakshmi_Kuppusamy_Thesis.pdf.
Повний текст джерелаPuschmann, Martin. "Anderson transitions on random Voronoi-Delaunay lattices." Doctoral thesis, Universitätsbibliothek Chemnitz, 2017. http://nbn-resolving.de/urn:nbn:de:bsz:ch1-qucosa-231900.
Повний текст джерелаDiese Dissertation behandelt Phasenübergange im Rahmen des Anderson-Modells der Lokalisierung in topologisch ungeordneten Voronoi-Delaunay-Gittern. Die spezielle Art der Unordnung spiegelt sich u.a. in zufälligen Verknüpfungen wider, welche aufgrund der restriktiven Gitterkonstruktion miteinander korrelieren. Genauer gesagt zeigt das System eine "starke Antikorrelation", die dafür sorgt, dass langreichweitige Fluktuationen der Verknüpfungszahl unterdrückt werden. Diese Eigenschaft hat in anderen Systemen, z.B. im Ising- und Potts-Modell, zur Abweichung vom universellen Verhalten von Phasenübergängen geführt und bewirkt eine Modifikation von allgemeinen Aussagen, wie dem Harris- and Imry-Ma-Kriterium. Die Untersuchung solcher Ausnahmen dient zur Weiterentwicklung des Verständnisses von kritischen Phänomenen. Somit stellt sich die Frage, ob solche Abweichungen auch im Anderson-Modell der Lokalisierung unter Verwendung eines solchen Gitters auftreten. Dafür werden insgesamt vier Fälle, welche durch die Dimension des Gitters und durch die An- bzw. Abwesenheit eines magnetischen Feldes unterschieden werden, mit Hilfe zweier unterschiedlicher Methoden, d.h. der Multifraktalanalyse und der rekursiven Greensfunktionsmethode, untersucht. Das Verhalten wird anhand der Existenz und Art der Phasenübergänge und anhand des kritischen Exponenten v der Lokalisierungslänge unterschieden. Für die vier Fälle lassen sich die Ergebnisse wie folgt zusammenfassen. In zweidimensionalen Systemen treten ohne Magnetfeld keine Phasenübergänge auf und alle Zustände sind infolge der topologischen Unordnung lokalisiert. Unter Einfluss des Magnetfeldes ändert sich das Verhalten. Es kommt zur Ausformung von Landau-Bändern mit sogenannten Quanten-Hall-Übergängen, bei denen ein Phasenwechsel zwischen zwei lokalisierten Bereichen auftritt. Für geringe Magnetfeldstärken stimmen die erzielten Ergebnisse mit den bekannten Exponenten v ≈ 2.6 überein. Allerdings wurde für stärkere magnetische Felder ein höherer Wert, v ≈ 2.9, ermittelt. Die Abweichungen gehen vermutlich auf die zugleich gestiegene Unordnungsstärke zurück, welche dafür sorgt, dass Elektronen zwischen verschiedenen Landau-Bändern streuen können und so nicht das kritische Verhalten eines reinen Quanten-Hall-Überganges repräsentieren. Im Gegensatz dazu ist das Verhalten in dreidimensionalen Systemen für beide Fälle ähnlich. Es treten in jedem System zwei Phasenübergänge zwischen lokalisierten und delokalisierten Bereichen auf. Für diese Übergänge wurde der Exponent v ≈ 1.58 ohne und v ≈ 1.45 unter Einfluss eines magnetischen Feldes ermittelt. Dieses Verhalten und die jeweils ermittelten Werte stimmen mit bekannten Ergebnissen überein. Eine Abweichung vom universellen Verhalten wird somit nicht beobachtet
Lippold, Georg. "Encryption schemes and key exchange protocols in the certificateless setting." Thesis, Queensland University of Technology, 2010. https://eprints.qut.edu.au/41697/1/Georg_Lippold_Thesis.pdf.
Повний текст джерелаNgo, Long. "Computationally sound automated proofs of cryptographic schemes." Thesis, Queensland University of Technology, 2012. https://eprints.qut.edu.au/54668/1/Long_Ngo__Thesis.pdf.
Повний текст джерелаBennett, Edmund. "Exotic order in magnetic systems from Majorana fermions." Thesis, University of St Andrews, 2016. http://hdl.handle.net/10023/9437.
Повний текст джерелаGorantla, Malakondayya Choudary. "Design and analysis of group key exchange protocols." Thesis, Queensland University of Technology, 2010. https://eprints.qut.edu.au/37664/1/Malakondayya_Gorantla_Thesis.pdf.
Повний текст джерелаAtas, Yasar Yilmaz. "Quelques aspects du chaos quantique dans les systèmes de N-corps en interaction : chaînes de spins quantiques et matrices aléatoires." Thesis, Paris 11, 2014. http://www.theses.fr/2014PA112221/document.
Повний текст джерелаMy thesis is devoted to the study of some aspects of many body quantum interacting systems. In particular we focus on quantum spin chains. I have studied several aspects of quantum spin chains, from both numerical and analytical perspectives. I addressed especially questions related to the structure of eigenfunctions, the level densities and the spectral properties of spin chain Hamiltonians. In this thesis, I first present the basic numerical techniques used for the computation of eigenvalues and eigenvectors of spin chain Hamiltonians. Level densities of quantum models are important and simple quantities that allow to characterize spectral properties of systems with large number of degrees of freedom. It is well known that the level densities of most integrable models tend to the Gaussian in the thermodynamic limit. However, it appears that in certain limits of coupling of the spin chain to the magnetic field and for finite number of spins on the chain, one observes peaks in the level density. I will show that the knowledge of the first two moments of the Hamiltonian in the degenerate subspace associated with each peak give a good approximation to the level density. Next, I study the statistical properties of the eigenvalues of spin chain Hamiltonians. One of the main achievements in the study of the spectral statistics of quantum complex systems concerns the universal behaviour of the fluctuation of measure such as the distribution of spacing between two consecutive eigenvalues. These fluctuations are very well described by the theory of random matrices but the comparison with the theoretical prediction generally requires a transformation of the spectrum of the Hamiltonian called the unfolding procedure. For many-body quantum systems, the size of the Hilbert space generally grows exponentially with the number of particles leading to a lack of data to make a proper statistical study. These constraints have led to the introduction of a new measure free of the unfolding procedure and based on the ratio of consecutive level spacings rather than the spacings themselves. This measure is independant of the local level density. By following the Wigner surmise for the computation of the level spacing distribution, I obtained approximation for the distribution of the ratio of consecutive level spacings by analyzing random 3x3 matrices for the three canonical ensembles. The prediction are compared with numerical results showing excellent agreement. Finally, I investigate eigenfunction statistics of some canonical spin-chain Hamiltonians. Eigenfunctions together with the energy spectrum are the fundamental objects of quantum systems: their structure is quite complicated and not well understood. Due to the exponential growth of the size of the Hilbert space, the study of eigenfunctions is a very difficult task from both analytical and numerical points of view. I demonstrate that the groundstate eigenfunctions of all canonical models of spin chain are multifractal, by computing numerically the Rényi entropy and extrapolating it to obtain the multifractal dimensions
Nguyen, Ngoc Bien. "Adaptation via des inéqualités d'oracle dans le modèle de regression avec design aléatoire." Thesis, Aix-Marseille, 2014. http://www.theses.fr/2014AIXM4716/document.
Повний текст джерелаFrom the observation Z(n) = {(Xi, Yi), i = 1, ..., n} satisfying Yi = f(Xi) + ζi, we would like to approximate the function f. This problem will be considered in two cases of loss function, Ls-risk and uniform risk, where the condition imposed on the distribution of the noise ζi is of bounded moment and of type sub-gaussian, respectively. From a proposed family of kernel estimators, we construct a procedure, which is initialized by Goldenshluger and Lepski, to choose in this family a final estimator, with no any assumption imposed on f. Then, we show that this estimator satisfies an oracle inequality which implies the minimax and minimax adaptive estimation over the anisotropic Hölder classes
Rangasamy, Jothi Ramalingam. "Cryptographic techniques for managing computational effort." Thesis, Queensland University of Technology, 2012. https://eprints.qut.edu.au/61007/1/Jothi_Rangasamy_Thesis.pdf.
Повний текст джерелаMEYER, HENDRIK. "Approches numeriques pour des modeles de physique statistique. I. Diagrammes de phase de modeles a spins. Ii. Theorie de matrices aleatoires et integrabilite." Université Joseph Fourier (Grenoble), 1996. http://www.theses.fr/1996GRE10239.
Повний текст джерелаSarkar, Pratik. "Adaptively Secure Primitives in the Random Oracle Model." Thesis, 2018. https://etd.iisc.ac.in/handle/2005/5449.
Повний текст джерелаGlazer, Victor. "Some results concerning security in the Random Oracle Model." 2005. http://link.library.utoronto.ca/eir/EIRdetail.cfm?Resources__ID=370141&T=F.
Повний текст джерелаHuang, Huang-ta, and 黃皇達. "A provably secure really source hiding designated verifier signature scheme based on random oracle model." Thesis, 2009. http://ndltd.ncl.edu.tw/handle/96656474628282582852.
Повний текст джерела南華大學
資訊管理學系碩士班
97
A lot of designated verifier signature (DVS) schemes have been proposed. However, all of them only provide the basic security requirement that only the designated verifier can check the validity of the signature. They are either not secure enough or lacking source hiding. Hence, in this article, we design a provably secure DVS scheme. It not only can attain the basic security requirement but also hide the original signer''s identity which makes our scheme more suitable for the applications in an electronic voting system.
Lee, Ming-Tsung, and 李明聰. "Implications of Quantum Mechanics based on a Random Medium Model and a Stochastic Micro-Phase-Space Formulation." Thesis, 2002. http://ndltd.ncl.edu.tw/handle/20811272010135150210.
Повний текст джерела國立臺灣大學
物理學研究所
90
Based on the framework of stochastic interpretation for quantum mechanics, two approaches are proposed to present several implications of quantum mechanics. One is the microscopic transport conservation approach for the random medium model. In this model, the quantum fluctuation of the microscopic object is assumed to arise from the collision between the microscopic object and the medion. Some assumptions for the object-medion collision are proposed to guarantee that the statistical ensemble manifestation of Schrodinger wave mechanics can be reproduced. According to this approach, several kinds of microscopic object energies and the local energy transport between the objects and the medions are studied. The other approach is the stochastic microscopic-phase-space formulation. A set of stochastic dynamic equations describing the motion of the individual object are proposed. According to this set of equations, a dynamic description for the von Neumann collapse is presented. Moreover, there exists the negativity of the microscopic-phase-space description in this formulation. The mechanism of the negativity is studied according to the stochastic dynamics. Some discussions on the significance of energy quantization and non-locality are also presented here.
Tiwari, Mayank. "Fully Resilient Non-Interactive ID-Based Hierarchical Key Agreement." Thesis, 2018. https://etd.iisc.ac.in/handle/2005/4080.
Повний текст джерелаIndian Institute of Science
Chethan, Kamath H. "Constructing Provably Secure Identity-Based Signature Schemes." Thesis, 2013. http://etd.iisc.ac.in/handle/2005/3330.
Повний текст джерелаChethan, Kamath H. "Constructing Provably Secure Identity-Based Signature Schemes." Thesis, 2013. http://etd.iisc.ernet.in/2005/3330.
Повний текст джерелаKurdestany, Jamshid Moradi. "Phases, Transitions, Patterns, And Excitations In Generalized Bose-Hubbard Models." Thesis, 2013. https://etd.iisc.ac.in/handle/2005/2563.
Повний текст джерелаKurdestany, Jamshid Moradi. "Phases, Transitions, Patterns, And Excitations In Generalized Bose-Hubbard Models." Thesis, 2013. http://hdl.handle.net/2005/2563.
Повний текст джерела






